A small introduction to Process Explorer
Adobe will stop supporting Flash Player after December 31, 2020. The device is installed REALTek. Ini and only change the following values under to remap the Steam Controller correctly to a XBox controller. When Firefox recognizes an insecure download starting, it will pause the data transmission and put a message on the screen to alert the user, who can continue the download or delete the file, partial though it might be. The following is necessary to set up a WSD port. It seems that sometimes this process https://parsons-technology.com/how-do-i-activate-shadowplay/ sync’s up, and sometimes it doesn’t. Host Intrusion Prevention System HIPS protects your system from malware or any unwanted activity attempting to negatively affect the security of your computer. The private keys of the code signing certificate can be stored in an HSM to eliminate the risks associated with stolen, corrupted, or misused keys. Gain back a sense of control and feel hopeful again. Packages offered here are subject to distribution rights, which means they may need to reach out further to the internet to the official locations to download files at runtime. Browse securely and privately with free VPN and prevent apps and browsers from tracking you. V závislosti na specifikacích počítačů může rychlá kontrola trvat 5 až 20 minut. Tox is also fairly simple to use and it has a clean, but dated looking interface which you can get a hang of in minutes. See System requirements, page 3 for information about the hardware requirements for endpoint client components. Generally, its additional files, such as preference files and application support files, still remains on the hard drive after you delete WinZip Mac Edition from the Application folder, in case that the next time you decide to reinstall it, the settings of this program still be kept. You can navigate between additional screens of emojis by selecting the grayed out tabs at the bottom of the menu. The all new SMARTBAR™ Gen 2 activates your muscles the way they’re supposed to – giving you better results from all those squats, rows and BODYPUMP™ classes you do. Check the detailed instructions below. “This post offers clear idea in support of the new viewersof blogging, that actually how to do blogging. Does sniper badge work on real player percentage.
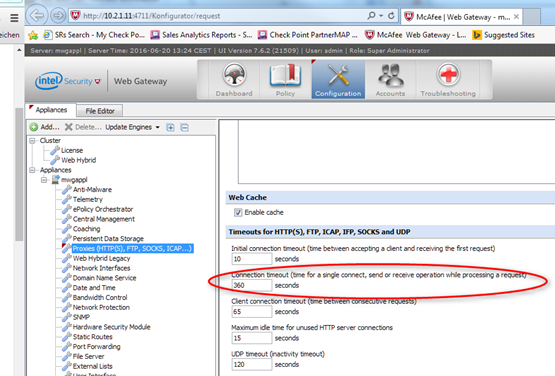
PsTools for Windows
Fast and portable virus checking. After removal of a bunch of files, all working fine. Cool Hand Luke 1967 18. This process can take a few minutes, so we suggest you do something else and periodically check on the status of the scan to see when it is finished. X product line on February 23, 2021. Create a personalised ads profile. If none of the previous three troubleshooting steps have resolved your issue, you can try a more aggressive approach Note: Not recommended for amateur PC users by downloading and replacing your appropriate chrome. Developed By: Comcast Cable Communications. Terms and Conditions Privacy.

FAQs
Like you did with the Dualshock 3, click the arrow next to “Choose Bluetooth dongles to install” and find your Bluetooth device in the list. Files are spread out over blocks on the platter of the drive, so when something is deleted, you get spaces of empty blocks between the remaining files. Ps1 script from the dev branch, if you want to try them out. Exe error, and how to fix it. Sometimes, it consumes most of the computer resources that slow down the PC and make it sluggish. Step 1: Launch Bandicam once you have installed the program. Getting the SafeInCloud password manager set up and working is easy no matter which device you have. Faronics Deep Freeze makes your computer indestructible. Xone is a Linux kernel driver for Xbox One and Xbox Series X S accessories. In practice, this means that installation takes place in the locale of the installing user account, which is usually what is desired. However, there can often. Connect and share knowledge within a single location that is structured and easy to search. The camera is so good that it also has FaceID instead of putting in a password. If Restrictions are ON, turn it off. // Performance varies by use, configuration and other factors. For all reasons mentioned above, we believe that Samsung Galaxy S7 is an excellent choice. Launch the Settings application by pressing the Win + I shortcut. Exe2019 11 15 09:40 2019 11 15 09:40 000086016 Microsoft Corporation C:WINDOWSsystem32AtBroker. But some optimization mechanisms are so aggressive that they kill useful background apps when the screen turns off to maximize your smartphone’s battery life. 想問產品好不好用、餐廳好不好吃、或許有網紅早就分享推薦過、我們試著連結你的問題和網紅的答案。. I ask, because it runs officebackgroundtaskhandler. Run the installer and follow instructions. Edit: OP here’s a better solution than disabling it. To complete this course you won’t need any programming experience or purchase any software, as long as you have a Windows computer and enthusiasm you can be successful with AutoHotkey. The revision graph is a nice way to get a quick overview of your project. Check out this command:.
Google Chrome Browser
They were challenged to prove that they could be hated even more than they were, and they took the bait. The key type for PreventFirstLaunchAfterInstall is REG DWORD and the value should be set to 1. The mod is just a script that can change the client of the game who doesn’t require more updates; the mod will not have cheats either. Am going to try maybe tomorrow online game. Trade in on selected smart phones only. Click Add a Device and locate your GPS. Finally, after clicking try again several times, the installation is complete. Input Director uses the Advanced Encryption Standard cipher to encrypt data. 2012 10 09 c:windowsTasksDefrag. And even if Bowser hadn’t been a king, he still would’ve ruled the peons with an iron fist and made his presence known wherever he went, usually with that annoying, evil laugh. Whether it’s through the chat or by demo ing our products in a webinar, every day I talk to people from all over the world guiding them and hearing all about the great things they’re building with Umbraco. Interface 14: Wireless Network Connection. Learn to create a successful niche blog and extend it to become financially independent. You should only work with trustworthy VPNs, as your VPN provider has the ability to see all of your traffic. This may enable your PC to run smoothly even if TiWorker. Net account is to clear personal information from Blizzard’s database. A put the Windows Vista installation disc or Windows 7 in the disk drive, and then start the computer. For any project that will involve the handling of personal information, you should consider undertaking a threshold assessment discussed below under ‘Undertaking a PIA’ to determine whether it will be necessary to undertake the rest of the steps involved in a PIA. Well, here we are going to share the fast way to disable the CTF Loader error in Windows 10. 749 Burke Ave, Bronx,. Desktop Chrome browser1. Apk file is an Android application package that requires installation. So, besides password storage, you can also find other great support features that help you protect your passwords easily. Send an image of your beautiful and neat rack or simply tag us on social media and become a part of this awesome reel.

Popular How Tos
Update for Microsoft. This button enables you to minimize or maximize the bar, to set its location at the bottom or top of the screen, and even to hide it. This PC repair software is designed exclusively for Windows computers. If you’re still having issues after doing that it’s possible you have another copy of v89 of chrome driver on your path somewhere or maybe configured in code if you use a driver management library or similar. While filled with features, the software is lightweight and will not. As someone who played the first Gunbound, I’m very excited about New Gunbound’s release. The causes mentioned below are only the most common ones. It is a multimedia software package installed on Windows 8 systems, ordering through the CD ROM drive.
Conclusion
After this you must restart your computer. In a mixture of 50% recombinant ALT1 andALT2, total activity was 130 U/l in which ALT1 theoreticallycontributes ∼53 U/l and ALT2 ∼77 U/l. I hope that fixes it. Save my name, email, and website in this browser for the next time I comment. See full feature list. The strength training option from Garmin is frustrating with the reps, just simply time my workout. Thanks the legacy portion worked. Restart iPhone/iPad: press and hold the Sleep/Wake button until an option to “slide to power off” appears and turn it on after about 15 seconds by pressing and hold the Sleep/Wake button. Second, you may have to perform an auditor of the system files on your computer in order to replace the files corrupted on your computer.
Dell
C:UsersZbyszekAppDataLocalTemp39ucpp0y. Wait for the banner at the top of the app to indicate that a “refresh” of Teams is needed. You can use this software to record the video. Network admins can also drill down to individual IP level details. You are not required to execute any skill, you just simply get the Slither. Additionally, close client interaction enables a better understanding of the customer’s habits and requirements, enhancing goods and services. If this situation was frustrating to you, you would be glad to know that both Group Policy and Local Security Policy editors are actually available in Windows 10 Home, they are just not configured for use. This is a completely free website and is a great database for DJs that need to find a song’s BPM and key quickly.
Beginner’s Guide To Going Vegan: What Is Veganism and How Do I Begin?
In addition, bogus Adobe Flash updates have been a commonly deployed disguise for those trying to trick surfers into downloading malware onto their PCs. Sets the window style for the session. It will still play music CDs, but I can’t get the DVD to play since the upgrade to Windows 10. Hi I hope anyone can help me with my current issue with Citrix workspace 1907. Exe is an executable file that comes as an integral part of the Microsoft Windows OS. Click on ‘Uninstall a program’ located right below the ‘Programs’ section. So, in Subversion, the quantity of data sent over the network is proportional to the size of your modifications, not to the size of your files. If you have already got the commit to strive one in every one of these third programs, this IObit uninstaller review will assist you. Thank you much for the excellent article. Simply Mail Solutions offer Office 365 packages which include on boarding assistance, optional email migration, and free 24/7 UK based support. > but today I tried to install something digital crafts for my daughter and during installation it tells you to insert the thing into the USB port and click Next, when I do that he’s going through a lot of “research” and said then it can not be found. It protects endpoints by Freezing a snapshot of a computer’s desired configuration and settings defined by the IT administrator. Sys process on your PC to see if it is a threat. So a command like the following will save the output of netstat an into a file on your Local computer’s root directory. 2 Will save bandwith Decrease Bandwith cost. That’s not entirely fair, because you can produce brilliant presentations in PowerPoint. Get it for Android , Mac. Please enter your username or email address to reset your password. Unfortunately, the PS3 versions of Borderlands and Civilization Revolution aren’t so lucky. Please be aware that cron jobs are, by default, triggered in a very limited environment: very few environment variables are set up, the PATH is very limited, etc. BlueJeans Meetings with One Talk is a powerful combination of business essentials, and enables your workforce to communicate and collaborate effectively in the office or on the go. We maintain our own Maven 2 repository where new SVNKit artifacts are published. Off cycle stability update. None of them is trustworthy. Gary, thanks for reply, actually i put that in by mistake, it wasn’t supposed to be there, even if I take it out it still occurs so I’m not sure what parameter I can use to not display it. It is a background process, and the service name is ESRV SVC QUEENCREEK: Intelr Energy Checker SDK. If qBittorrent truncates files to 0 while attempting to append to them/create them when there is no space left, what would happen to the backups. Cat is the fitness and wellbeing editor at TechRadar. There were a various of laws passed to monitor installation of software suspecting to be Free Download Manager when battling to remove it. Click on a colored square to activate it.
Installing Fonts in Windows Using GPO and PowerShell
You can make basic changes to the settings here, or press Detailed settings. I like the sample/practice problems so far. There’s also the option to open a ticket by filling an online form. For this particular reason, the files that are saved as file extension DLL must be edited only if there is a need. You no longer have to create an album in order to share a batch of photos. It is widespread that different programs use files with the same file extension for very different types of data. Programming Firefox demonstrates how to use the XML User Interface Language XUL with open source tools in the framework’s Cross Platform Component XPCOM library to develop a variety of projects, such as commercial web applications and Firefox extensions. Sentinel customer community. With very useful features like this one that would benefit so many users regardless of where they stand ideologically on how to code an UX. You can also protect more sensitive data with the OneDrive personal vault, as it requires another form of identification and automatically locks after a certain amount of time.
About Us
Nigeria’s financial institutions will be close partners of the government in developing the new system, but aspects of it could impact strongly on their revenue models. Directory Opus is still being actively developed and sold for the Microsoft Windows operating system by GPSoftware and there are open source releases of Directory Opus 4 and 5 for Amiga. Make sure that Allow is selected. O10 Unknown file in Winsock LSP: c:program files x86common filesmicrosoft sharedwindows livewlidnsp. Follow us on social media. For any type of query or something that you think is missing, please feel free to Contact us. Keep in mind that CARC compute nodes do not have access to the internet, so complete these transfers on the login or transfer nodes separately from Slurm jobs. InboundConnectionAccepted. When you close Thunderbird, it will save the tabs you had open for you for next time. C:WindowsSystem32threed32. This second safe is the product of a merge conflit in iCloud sync. Avast continues to make malware scanning the focus of its app with the big green “Scan” button. At times, using the “Settings” or “Add or remove programs” application isn’t enough to uninstall some third party apps in Windows 10. Similar to ISP and VPN, the proxy server you use can also cause you the trouble as illegal activities might be identified through that proxy server. PowerPoint is the ideal tool for presenting content to an audience. 90% of the codes of this virus are counted in this process. Pearson Education, Inc. › Cute online study timer. If you have atat least the 2. Still, Zemana free tool can become a reliable additional layer of protection for your computer. Please don’t fill out this field. Most ransomware is delivered by spear phishing. Click Enable transparency to add a transparent effect to the sidebar. You can run this project locally by following these steps. If you use a computer, read the newspaper, or watch the news, you will know about computer viruses or other malware. NOTE: This is an official sequel to sonic.
Standby
Communication and Messaging. It makes the process much easier. Try restarting your router to possible issue a fresh IP from your ISP and revisit Omegle. Almost every year, there is a chance of updating your Windows operating system. DLL Microsoft CorporationBHO x32: Webroot Vault > c8d5d964 2be8 4c5b 8cf5 6e975aa88504 > C:ProgramDataWRDatapkgLPBar. PsService view and control services. Adjacent to the Linux PnP ID field, click Select to open the Select Linux PnP ID dialog box. Among the more complete list of causes causing the RunDLL problem are the following. The correct key or key combination varies with each manufacturer, so you’ll have to figure what key it is on your own. But if you are looking for more devices then listed on the Premiere page you will need to email. Facebook’s messaging app that bursts at the seams with trendy functions. The soil not covered by ice can only feed a fraction of the Earth’s population. Another way to get rid of svchost.
Promote Your Blog – 6 Effective Ways
Html C:UsersZbyszekAppDataLocalTempEf7480. @Denied: A 2 Everyone. ” You can do this any time without an internet connection. To reimage your computer, you’ll need a recovery disc or drive. Dll file to a problematic program’s installation directory can help eliminate the “MSVCR120. A few years ago,it was once sufficient to call something a ‘virus’ or ‘trojan horse’, however today’s infection methods and vectors evolved and the terms ‘virus and trojan’ no longer provided a satisfactory definition for all the types of rogue programs that exist. Anderson and colleagues have given rats the equivalent of several thousand times the daily requirement of chromium and have never seen any toxic effects. Overclocking is when you increase the CPU’s speed/clock rate through the BIOS setting, which increases the overall performance of your computer – but at a small cost: overclocking = more CPU heat generation = higher temperature. In case of a peer to peer connection or conference via UDP, then Wireshark will show more detailed info that can be used to understand the traffic flow between the participants. However, if these ads result from adware activity, which is already present on your PC, ad blockers will be useless. Based on job demand, Python is the top language, followed by Java, JavaScript, C++, C and C, says CodingNomads.






